BLACK BOX
A Pentest® is a security resistance test against an information system, application or security scheme, etc. And this type of test is generally carried out in a BLACK BOX mode, that is, without privileged information about the target or, in other words, simulating a real scenario of an external attacker who must start from scratch.
Pentest® has been carrying out this type of testing for all types of organizations and companies over the last 20 years. Although a BLACK BOX test does not guarantee the safety of your assets, it is a very effective way to stress your defense mechanisms.
On the other hand, since this service does not require the transfer of information about the details of the target architecture, it is the easiest to contract and its preparation is the simplest.
And how good are we at these BLACK BOX tests? Well, imagine: Pentest® is the acronym for "PENETRATION TESTING", our brand, trade name, domain name and identity sign of a service that we have been offering for two decades and that has been gaining interest from companies all around the World.
If you need an independent and realistic examination, an opinion based 100% on in-depth and verifiable knowledge, we are one of the best companies you can hire. Contact us and we will assist you quickly and efficiently to resolve any questions you may have about the details of the execution of the service, its cost, etc. And if we cannot help you, we will recommend the best ones among our competitors.
Get a quote in 24h
ContactWHITE BOX
A WHITE BOX test is an evaluation of the security of a target with detailed information beforehand.
In this type of test we will ask you for very specific data about your solution. If it is a test of a corporate network, we will want to have a detailed topology, information about firewall policies, about servers and workstations, software that is running, versions, etc. If the target is a specific application, we will ask for access to the source code, technical documentation with architecture details, etc.
The goal of this kind of testing is an in-depth review focusing resources on inspecting the points that by design have the most options of being or becoming a weak link that potential attackers can take advantage of.
What's the point of a security resistance test if you are going to provide us with all the details of your security solution? Well, a lot. In a WHITE BOX test, we can offer reliable evidence of the danger posed by the current defenses implemented in your organization or application, through the practical exploitation of the weak points that we can identify when evaluating the design. Basically we will demonstrate what you probably always suspected could happen, giving you some excellent arguments to present to company management. At the same time we will offer you solutions for many more weak points than a BLACK BOX test: design solutions.
Remember that at Pentest® we are specialized in finding flaws in security solutions. Therefore, access to the details of your architecture allows us to give enormous added value to the service by being able to provide you with tailored solutions based on knowledge of the internal details of your own reality and not more generic solutions like those usually offered in a BLACK BOX test.
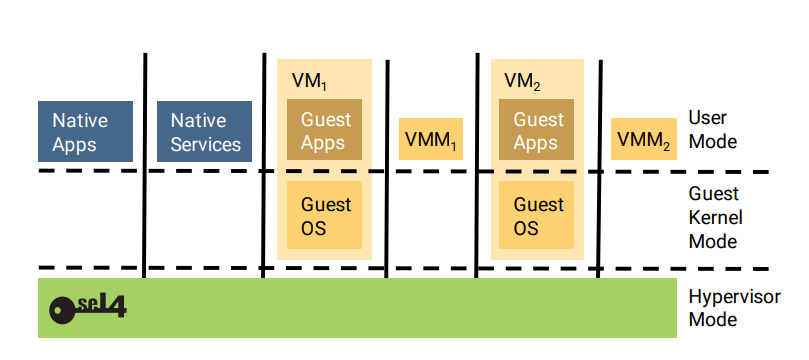
seL4 DEVELOPMENTS
seL4 is a micro kernel that has been formally verified (https://sel4.systems/About/seL4-whitepaper. pdf) and whose security is therefore beyond all debate. At Pentest we are pioneers in Spain developing security solutions based on seL4.
If you want a solution that practically requires no maintenance (patches and security updates, etc.) then seL4 is the most robust option that exists today since its ability to isolate processes and complete operating systems has been mathematically corroborated making it perfect for creating information systems where genuine guarantees are required and not based on just marketing.
With seL4 as our solutions flagship at Pentest, we create custom software that will allow you to offer any service you can imagine, from embedded systems for specific hardware to Cloud services, with a level of security never before achieved by any other manufacturer. .
Contact us
admin@pentest.es
C\Uruguay, Parcela 13, Pol. Ind. Oeste
Alcantarilla – 30820 (Murcia), SPAIN
Tlf. : (+34) 868 952 259
*Informative note: all the data that you provide us will be treated with total confidentiality and adopting the necessary security measures in compliance with current legislation.